HCI Box on a Budget. Leverage Azure Spot & Hyrbrid Use Benefits. Up to 93% savings.
Do you want to take HCI Box for a test drive but dont have $2,681 in the budget? Me either. How about the same box for $178?
This is the price for 730 hours
Following general instructions from jumpstart Azure Arc Jumpstart
once you have the git repo, edit the host.bicep file
...\azure_arc\azure_jumpstart_hcibox\bicep\host\host.bicep
add to the properties for the host virtualMachine the resource vm 'Microsoft.Compute/virtualMachines@2022-03-01'
priority: 'Spot'
evictionPolicy: 'Deallocate'
billingProfile: {
maxPrice: -1
}You can review difference regions for either cheaper price per hour or lower eviction rate
0.24393 per hour * 730 hours = $178
If you are elegable for Hybrid Use Benefits through you EA or have licenses you can also enable HUB in the Bicep template under virtual machine properties
licenseType: 'Windows_Server'
Code changes
...
resource vm 'Microsoft.Compute/virtualMachines@2022-03-01' = {
name: vmName
location: location
tags: resourceTags
properties: {
licenseType: 'Windows_Server'
priority: 'Spot'
evictionPolicy: 'Deallocate'
billingProfile: {
maxPrice: -1
}
...Good luck, enjoy HCI’ing
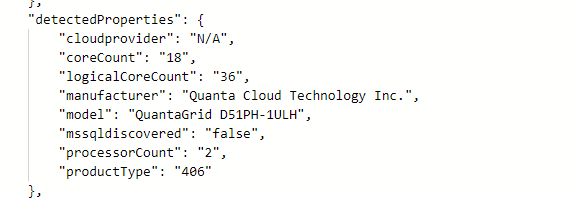
Interesting changes to Arc Agent 1.34 with expanded detected properties
Microsoft just pushed out a change in Azure Arc Connected Agent 1.34 and with this comes some enrichment of Hybrid Servers detected properties.
This is what the properties looked like prior to the update.
Agent 1.33 and earlier
Okay… so what’s new and different?
New detected properties for Azure Arc Connected Agent 1.34
serialNumber, ProcessNames and totalPhysicalMemory
resources
| where ['type'] == "microsoft.hybridcompute/machines"
| extend processorCount = properties.detectedProperties.processorCount,
serialNumber = properties.detectedProperties.serialNumber,
manufacturer= properties.detectedProperties.manufacturer,
processorNames= properties.detectedProperties.processorNames,
logicalCoreCount = properties.detectedProperties.logicalCoreCount,
smbiosAssetTag = properties.detectedProperties.smbiosAssetTag,
totalPhysicalMemoryInBytes = properties.detectedProperties.totalPhysicalMemoryInBytes,
totalPhysicalMemoryInGigabytes = properties.detectedProperties.totalPhysicalMemoryInGigabytes
| project name,serialNumber,logicalCoreCount,manufacturer,processorCount,processorNames,totalPhysicalMemoryInBytes,totalPhysicalMemoryInGigabytes
This unlocks organizations to collect processor, serial number and memory information in a simple fashion via Azure Arc infrastructure. This can be used to look at things like consolidation and migration planning, perhaps decommissioning aging hardware even warranty lookup if you don’t have current hardware CMDB.
SQL Counters via Azure Arc
Walk through how to collect SQL counter using Data collection Rule and displaying the results on a workbook an Azure Dashboard.
Microsoft is rapidly expanding the services and features available from the Azure Arc SQL Extension. As this moves into GA and more visibility features get added and importantly, features that allow actions EG controlling backup and even patching using Azure to create a management layer for your SQL Server estate outside of Azure becomes more viable.
Let’s take a brief look at grabbing SQL-specific performance counters to Azure Monitor Metrics.
We need to create a Data Collection Rule (DCR). I am not using Data Collection Endpoints (DCE), but you may want to consider this in your environment.
Select the Arc Resource you want to add
now we need to add some Performance counter
it will add a bunch by default; select None, then Custom to clear all.
Unfortunately, currently, you can not see the SQL counters from this view, so you’ll have to go collect what you want from another source.
You can use Perfmon, unfortunately you cant copy from perfmon.
this query will provide a list
SELECT COUNT(*) FROM sys.dm_os_performance_counters;
Here is a list I have extracted for this DCR
\SQLServer:General Statistics\User Connections \SQLServer:General Statistics\Logins/sec \SQLServer:General Statistics\Transactions \SQLServer:Databases(_Total)\Active Transactions \SQLServer:SQL Statistics\Batch Requests/sec \SQLServer:SQL Statistics\Logical Connections \SQLServer:SQL Statistics\SQL Compilations/sec \SQLServer:SQL Statistics\SQL Re-Compilations/sec
Paste it in line by line, Add, tick, Delete line, next counter. Adjust the Sample rate as needed. I have used the default 60 seconds. For large SQL servers estates, you might want to consider increasing this depending on your needs.
It’s worth considering building a template for this if you want to do this repeatedly. This resource type has some challenging layers to work through for deployment. Microsoft reference material can be found here.
we pipe these into Azure Monitor Metrics Which is still in preview and for this exercise I will also push the data into a log analytics instance.
as of this writing the metrics for hybrid compute fail to be added to scope of Azure Monitor. For the remainder of this example we will use Log Analytics Workspace for metrics.
Heading over to the Log Analytics Workspace. You can create various Kusto queries to integrate these SQL Metrics
Perf
| where ObjectName == 'SQLServer:General Statistics' and CounterName == 'User Connections'
| project TimeGenerated, Computer, ObjectName, CounterName, CounterValue
| summarize avg(CounterValue) by bin(TimeGenerated,60m) , Computer
| render timechartYou can send this to a Workbook or Dashboard
We can now see the data on a chart in a workbook. By saving the you can give the workbook a name and save it to a resource group
Alternatively, you can publish this to an Azure Dashboard. I am going to use the dashboard I created here Arc SQL Extension - Best Practices Assessment — Crying Cloud
This displays a tile here. You can continue to add tiles and edit the queries. You build workbooks and dashboards to target the specific metrics about your Arc-enabled SQL Servers.
Azure Arc delivers SQL Databases as Resources in Azure
The SQL extension for Arc-connected servers itself isn’t new, however, it has had a new feature added that is currently in preview; which is the ability to create Azure resources that represent your SQL Database through the Arc-connected Servers.
You can see this will detect objects for SQL instances, named SQL instances, and the databases themselves become objects in Azure
If you already have this installed this is one configuration setting you may want to check and that is “Has NT AUTHORITY\SYSTEM in the sysadmin role.” This is listed in the prerequisites of the install instructions that can be found here View SQL Server databases - SQL Server | Microsoft Learn
It is worth noting this currently works only for the Microsoft.HybridCompute type and not for example the VMware connected Arc systems Microsoft.ConnectedVMwarevSphere.
There are some properties here listed as unknown however, this is a bug that has already been fixed.
This is the next step to bringing SQL databases into the Azure control plane, creating alerts on recovery models, encryption state, or perhaps statistic creation. Enabling more visibility and control into the Hybrid Cloud journey.
This is the first public preview of this feature and I’ll definitely be keeping an eye out for future revisions and enhancements.
MAAS Image Builder Exclude Update by KB#
This briefly shows how to alter the image builder scripts to exclude broken KBs for specific OS versions. This example shows excluding Cumulative Update for Windows 11 Insider Preview (KB5019765) on an HCI image.
Trying to build a newer HCI Maas image and receive an error trying to download an update via release channel. Specifically, Windows 11 insider preview KB5019765
If you edit the Logon.ps1 found in the UnattendedResource folder from cloudbase/windows-imaging-tools: Tools to automate the creation of a Windows image for OpenStack, supporting KVM, Hyper-V, ESXi and more. (github.com) you can see there is a section that allows you to create a blacklist of KBs for different OS version.
Using PowerShell [System.Environment]::OSVersion.Version you can find the OS version
Finally add a record for the OS version and KB you want to exclude
Which is displayed via verbose output during build
Topic Search
-
Securing TLS in WAC (Windows Admin Center) https://t.co/klDc7J7R4G
Posts by Date
- March 2025 1
- February 2025 1
- October 2024 1
- August 2024 1
- July 2024 1
- October 2023 1
- September 2023 1
- August 2023 3
- July 2023 1
- June 2023 2
- May 2023 1
- February 2023 3
- January 2023 1
- December 2022 1
- November 2022 3
- October 2022 7
- September 2022 2
- August 2022 4
- July 2022 1
- February 2022 2
- January 2022 1
- October 2021 1
- June 2021 2
- February 2021 1
- December 2020 2
- November 2020 2
- October 2020 1
- September 2020 1
- August 2020 1
- June 2020 1
- May 2020 2
- March 2020 1
- January 2020 2
- December 2019 2
- November 2019 1
- October 2019 7
- June 2019 2
- March 2019 2
- February 2019 1
- December 2018 3
- November 2018 1
- October 2018 4
- September 2018 6
- August 2018 1
- June 2018 1
- April 2018 2
- March 2018 1
- February 2018 3
- January 2018 2
- August 2017 5
- June 2017 2
- May 2017 3
- March 2017 4
- February 2017 4
- December 2016 1
- November 2016 3
- October 2016 3
- September 2016 5
- August 2016 11
- July 2016 13