Interesting changes to Arc Agent 1.34 with expanded detected properties
Microsoft just pushed out a change in Azure Arc Connected Agent 1.34 and with this comes some enrichment of Hybrid Servers detected properties.
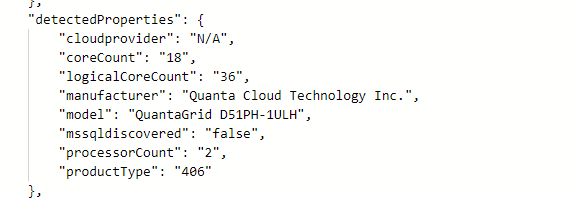
This is what the properties looked like prior to the update.
Agent 1.33 and earlier
Okay… so what’s new and different?
New detected properties for Azure Arc Connected Agent 1.34
serialNumber, ProcessNames and totalPhysicalMemory
resources
| where ['type'] == "microsoft.hybridcompute/machines"
| extend processorCount = properties.detectedProperties.processorCount,
serialNumber = properties.detectedProperties.serialNumber,
manufacturer= properties.detectedProperties.manufacturer,
processorNames= properties.detectedProperties.processorNames,
logicalCoreCount = properties.detectedProperties.logicalCoreCount,
smbiosAssetTag = properties.detectedProperties.smbiosAssetTag,
totalPhysicalMemoryInBytes = properties.detectedProperties.totalPhysicalMemoryInBytes,
totalPhysicalMemoryInGigabytes = properties.detectedProperties.totalPhysicalMemoryInGigabytes
| project name,serialNumber,logicalCoreCount,manufacturer,processorCount,processorNames,totalPhysicalMemoryInBytes,totalPhysicalMemoryInGigabytes
This unlocks organizations to collect processor, serial number and memory information in a simple fashion via Azure Arc infrastructure. This can be used to look at things like consolidation and migration planning, perhaps decommissioning aging hardware even warranty lookup if you don’t have current hardware CMDB.
Feature Parity for Azure Arc Server Resource Types?
When is an Azure Arc Server; not an Arc Server? A look at Azure Arc Server Resource types and the lack of feature parity between them
This is an Azure Arc Server (Server)
This is an Azure Arc Server (VMware)
This is an Azure Arc Server (HCI)
Introduction
Yes! Yes, Same Same… but different. Okay, so what? Not all Azure Arc Server VM objects are created equal. If we look a little closer at the Azure Resource Types we can see there are three different types listed here;
(Server) "type": "Microsoft.HybridCompute/machines"
(VMWare) "type": "microsoft.connectedvmwarevsphere/virtualmachines"
(HCI) "type": "microsoft.azurestackhci/virtualmachines"
Each of these types connecting via different methods to your Azure subscriptions, and along with this comes different functionality.
Server Blades
Let’s take a cursory look at (Server) using the standard connected Azure Connected Machine Agent. Lots of information, server, patch level, settings, operations, monitoring, big buttons to click great, appears feature rich and has the feel of Azure…. what’s your point?
Take note of the menu options on the left. You can also click on an image to enlarge it.
Okay, how about (VMWare)? It seems to be missing a few options and capability compared to the Server.
Well, what about (HCI)? Huh … It seems like its missing even more options.
VM Extensions
Unfortunately, this isn’t where the differences end. Taking a closer look at the Extensions available for each resource type. In particular, let’s say you want to start taking advantage of the new functionality around Arc-Enabled SQL Servers. Now the Arc SQL Extension is meant to Auto install… but only if you are using the (Server) type that is "type": "Microsoft.HybridCompute/machines"
Extension for (Server)
For the other two types, that Arc SQL Server extension is missing.
Extension for (VMware)
Extensions for (HCI)
HCI and VMWare
It is touted that it is easy to install Azure Arc for for your entire vSphere farm, and they are not wrong, you can import up to a maximum of 9500 VMs if you like with very little effort… up front. But you are not being offered all the benefits of an Azure Arc Server. You cant have the Arc SQL extension to monitor, operate and control your SQL Servers anywhere.
Digging into an HCI Cluster, you can Arc-enable the host nodes. These actually appear as first-class citizens of Azure as Azure Arc Servers.
Here is the cluster
and here is one of those nodes.
Here is where you would start the setup for the HCI Resource Bridge Setup, and through this is where you connect servers the HCI clusters guests.
but while the hosts have the full feature set of an Arc Server the HCI cluster guest VMs don’t.
VMware and HCI types are seriously lagging behind Arc Server and missing features and are essentially second-class citizens of Azure compared to the original HybridCompute resource type. You can See Updates, Azure Monitor, and SQL Extensions are all only available for Azure Arc (Server).
Resource Explorer
Through the Resource Explorer in the Azure Portal we can see the different types and more specifically the different ways they have been enabled. (Server)
We can see the (VMWare) which has a number of operations at the cluster level
and (HCI) which also has more operations at the cluster level than at the VM level.
Conclusion
Of course, you can’t install multiple types on the same server. I believe Azure Arc (Server) is the only way to go. Seeing the lack of parity in functionality between these types, it’s worth creating a method to deploy Azure Connected Agent directly on the machine yourself and at scale rather than leveraging time savings tools with the Resource Bridge that allow easy onboarding of vSphere and HCI cluster guests which leverage the Arc Resource Bridge.
That’s not to say the Resource Bridge isn’t useful for K8s or Arc Data Services. However, you should be aware of the lack of feature parity for HCI or VMWare installations of Arc Server Resource Type and make an informed decision about which Resource Type of Azure Arc Server you need or want in your environment.
SQL Counters via Azure Arc
Walk through how to collect SQL counter using Data collection Rule and displaying the results on a workbook an Azure Dashboard.
Microsoft is rapidly expanding the services and features available from the Azure Arc SQL Extension. As this moves into GA and more visibility features get added and importantly, features that allow actions EG controlling backup and even patching using Azure to create a management layer for your SQL Server estate outside of Azure becomes more viable.
Let’s take a brief look at grabbing SQL-specific performance counters to Azure Monitor Metrics.
We need to create a Data Collection Rule (DCR). I am not using Data Collection Endpoints (DCE), but you may want to consider this in your environment.
Select the Arc Resource you want to add
now we need to add some Performance counter
it will add a bunch by default; select None, then Custom to clear all.
Unfortunately, currently, you can not see the SQL counters from this view, so you’ll have to go collect what you want from another source.
You can use Perfmon, unfortunately you cant copy from perfmon.
this query will provide a list
SELECT COUNT(*) FROM sys.dm_os_performance_counters;
Here is a list I have extracted for this DCR
\SQLServer:General Statistics\User Connections \SQLServer:General Statistics\Logins/sec \SQLServer:General Statistics\Transactions \SQLServer:Databases(_Total)\Active Transactions \SQLServer:SQL Statistics\Batch Requests/sec \SQLServer:SQL Statistics\Logical Connections \SQLServer:SQL Statistics\SQL Compilations/sec \SQLServer:SQL Statistics\SQL Re-Compilations/sec
Paste it in line by line, Add, tick, Delete line, next counter. Adjust the Sample rate as needed. I have used the default 60 seconds. For large SQL servers estates, you might want to consider increasing this depending on your needs.
It’s worth considering building a template for this if you want to do this repeatedly. This resource type has some challenging layers to work through for deployment. Microsoft reference material can be found here.
we pipe these into Azure Monitor Metrics Which is still in preview and for this exercise I will also push the data into a log analytics instance.
as of this writing the metrics for hybrid compute fail to be added to scope of Azure Monitor. For the remainder of this example we will use Log Analytics Workspace for metrics.
Heading over to the Log Analytics Workspace. You can create various Kusto queries to integrate these SQL Metrics
Perf
| where ObjectName == 'SQLServer:General Statistics' and CounterName == 'User Connections'
| project TimeGenerated, Computer, ObjectName, CounterName, CounterValue
| summarize avg(CounterValue) by bin(TimeGenerated,60m) , Computer
| render timechartYou can send this to a Workbook or Dashboard
We can now see the data on a chart in a workbook. By saving the you can give the workbook a name and save it to a resource group
Alternatively, you can publish this to an Azure Dashboard. I am going to use the dashboard I created here Arc SQL Extension - Best Practices Assessment — Crying Cloud
This displays a tile here. You can continue to add tiles and edit the queries. You build workbooks and dashboards to target the specific metrics about your Arc-enabled SQL Servers.
"CannotChangeInventoryId is not allowed" Enabling a VMWare OS template in Azure via VMWare Arc-Connected vSphere
While working on a VMware Arc-connected instance of vSphere I had an issue enabling a template for use in Azure. I had created a template deleted it then tried to recreate it with the same name and received the following error.
{"code":"DeploymentFailed","message":"At least one resource deployment operation failed. Please list deployment operations for details. Please see https://aka.ms/DeployOperations for usage details.","details":[{"code":"CannotChangeInventoryId","message":"Resource 'template-Win2019STD' was previously configured with InventoryItemId 'vmtpl-vm-2015'. Changing InventoryItemId is not allowed."}]}
In the resource group and select show hidden items, we can see a template with that name
if we actually look at the object or JSON view we can see this is the ID from the error
simply delete the template causing the issue
Now when you try to “Enable in Azure” it should work.
This also works with the other VMware types that can be enabled.
Update Management Center and Azure Arc for Linux Server Patch Management
Let’s say you want to redeploy some of your on-premises servers for a Kubernetes cluster or LXD cluster. In our MAAS portal we can select the appropriate ‘Ready’ systems we want to deploy. In this demonstration we have a range of different hardware selected here, an HP blade 460c, a dell blade M630, a Cisco C220, and 2 Quanta boxes.
Select desired OS and Release
check ‘Cloud-init user-data
Paste in the Azure Arc Connected script. You need to include the bash header ‘#!/bin/bash’.
Start deployment
Linux Bash script for reference. This was generated by the Azure Portal using an onboarding agent. You can find more details about this here Azure Arc & Automanage for MAAS — Crying Cloud
#!/bin/bash
# Add the service principal application ID and secret here
servicePrincipalClientId="xxxxxx-xxx-xxx-xxx-xxxxxxx"
servicePrincipalSecret="xxxxxxxxxxxxxxxxxxxxxxxx"
export subscriptionId=xxxxxx-xxxxx-xxx-xxx-xxxxxx
export resourceGroup=ArcResources
export tenantId=xxxxx-xxxx-xxx-xxxx-xxxxxx
export location=eastus
export authType=principal
export correlationId=d208f5b6-cae7-4dfe-8dcd-xxxxxx
export cloud=AzureCloud
# Download the installation package
output=$(wget https://aka.ms/azcmagent -O ~/install_linux_azcmagent.sh 2>&1)
if [ $? != 0 ]; then wget -qO- --method=PUT --body-data="{\"subscriptionId\":\"$subscriptionId\",\"resourceGroup\":\"$resourceGroup\",\"tenantId\":\"$tenantId\",\"location\":\"$location\",\"correlationId\":\"$correlationId\",\"authType\":\"$authType\",\"messageType\":\"DownloadScriptFailed\",\"message\":\"$output\"}" https://gbl.his.arc.azure.com/log &> /dev/null; fi
echo "$output"
# Install the hybrid agent
bash ~/install_linux_azcmagent.sh
# Run connect command
sudo azcmagent connect --service-principal-id "$servicePrincipalClientId" --service-principal-secret "$servicePrincipalSecret" --resource-group "$resourceGroup" --tenant-id "$tenantId" --location "$location" --subscription-id "$subscriptionId" --cloud "$cloud" --correlation-id "$correlationId"You may also find it useful to Tag the servers with a project name and possibly lock them.
Added a tag ‘ArcConnected’ and you can see all the other automatic tags added by MAAS
And we can see the servers locked in MAAS
Importantly you can see the servers added to Azure Portal as Arc Servers
Drilling into one of the servers we can see the name assigned by MAAS, the OS we chose to deploy, the hardware model, agent version, etc.
Depending on your needs you can do a range connect it to Azure ‘Automanage’ or to ‘Update management center’ for instance. Lets go ahead and configure patches through Update Management Center (currently in preview)
As the assessments finish, we can see the updates for the on-premise servers through the Azure portal for each of the servers
Update settings to Enable Periodic Assessment every 24 hours is optional
Next, we can ‘Schedule updates’ and create a repeating schedule
ensure that we select our on-premise servers, and define what type of patches. In this case we only want to push Critical Updates and Security patches. If you select other Linux patches Azure will patches things like snaps and you may want to do those type of patches in a more controlled manor.
You can browse the ‘Maintenance Configuration’ and make any necessary changes
We can validate update history using the portal also.
We have deployed Ubuntu servers using MAAS, connected them to Azure using Azure Arc during installation with scripted onboarding, viewed missing updates, scheduled daily assessments, and created a repeating schedule to ensure critical updates and security patches are pushed to these systems.
This method could be used to manage systems in any other cloud system, bringing the management of Linux patching into the Azure control plane
This is a small window into what can be done using Azure Arc to help with operational activities in a Hybrid cloud environment
Topic Search
-
Securing TLS in WAC (Windows Admin Center) https://t.co/klDc7J7R4G
Posts by Date
- March 2025 1
- February 2025 1
- October 2024 1
- August 2024 1
- July 2024 1
- October 2023 1
- September 2023 1
- August 2023 3
- July 2023 1
- June 2023 2
- May 2023 1
- February 2023 3
- January 2023 1
- December 2022 1
- November 2022 3
- October 2022 7
- September 2022 2
- August 2022 4
- July 2022 1
- February 2022 2
- January 2022 1
- October 2021 1
- June 2021 2
- February 2021 1
- December 2020 2
- November 2020 2
- October 2020 1
- September 2020 1
- August 2020 1
- June 2020 1
- May 2020 2
- March 2020 1
- January 2020 2
- December 2019 2
- November 2019 1
- October 2019 7
- June 2019 2
- March 2019 2
- February 2019 1
- December 2018 3
- November 2018 1
- October 2018 4
- September 2018 6
- August 2018 1
- June 2018 1
- April 2018 2
- March 2018 1
- February 2018 3
- January 2018 2
- August 2017 5
- June 2017 2
- May 2017 3
- March 2017 4
- February 2017 4
- December 2016 1
- November 2016 3
- October 2016 3
- September 2016 5
- August 2016 11
- July 2016 13